In the digital age, securing online communications is essential. One of the most widely used protocols to achieve this is Transport Layer Security (TLS). This article provides a comprehensive introduction to TLS, explaining its purpose, how it works, and its significance in various applications.
What is TLS?
Transport Layer Security (TLS) is a cryptographic protocol designed to provide secure communication over a computer network. It ensures that data transmitted between applications, such as web browsers and servers, remains confidential and integral. TLS is the successor to the Secure Sockets Layer (SSL) protocol, offering enhanced security features.
The Evolution of TLS
TLS evolved from SSL, which was developed by Netscape Communications Corporation in the mid-1990s to secure web sessions. Over time, vulnerabilities were discovered in SSL, leading to the development of TLS. The first version of TLS, TLS 1.0, was published in 1999. Subsequent versions, including TLS 1.1, 1.2, and the latest, TLS 1.3, have introduced improvements in security and performance.
Why is TLS Important?
TLS plays a crucial role in protecting sensitive information transmitted over the internet. Without TLS, data such as passwords, credit card numbers, and personal messages could be intercepted and read by unauthorized parties. By encrypting data, TLS ensures that even if the data is intercepted, it remains unreadable to attackers.
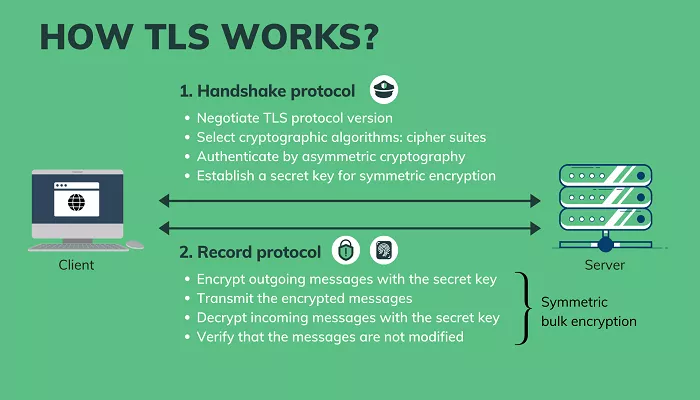
How Does TLS Work?
TLS operates through a series of steps to establish a secure connection between a client and a server:
- Handshake: The client and server exchange messages to agree on encryption algorithms and establish a secure connection.
- Authentication: The server provides a digital certificate to prove its identity. Optionally, the client may also provide a certificate to authenticate itself to the server.
- Session Key Generation: Both parties generate a shared secret key, known as the session key, used to encrypt and decrypt the data during the session.
- Data Transmission: Encrypted data is exchanged between the client and server using the session key.
- Session Termination: Once the communication is complete, the session is terminated, and the session key is discarded.
TLS Versions and Their Features
- TLS 1.0: Introduced in 1999, TLS 1.0 was the first version of the protocol. It is now considered outdated and insecure.
- TLS 1.1: Released in 2006, TLS 1.1 addressed some vulnerabilities found in TLS 1.0. However, it is also considered obsolete and is no longer widely supported.
- TLS 1.2: Published in 2008, TLS 1.2 introduced stronger encryption algorithms and improved security features. It remains widely used today.
- TLS 1.3: The latest version, TLS 1.3, was finalized in 2018. It offers enhanced security and performance by reducing the number of round trips required during the handshake and removing outdated cryptographic algorithms.
TLS in Everyday Applications
TLS is used in various applications to secure communications:
- Web Browsing: When you visit a website with “https://” in the URL, TLS is used to encrypt the connection between your browser and the server.
- Email: TLS secures email transmissions, ensuring that messages are not intercepted during transit.
- File Transfers: Protocols like FTPS and SFTP use TLS to protect files being transferred over the internet.
- Virtual Private Networks (VPNs): Some VPNs utilize TLS to establish secure tunnels for data transmission.
TLS and VPNs
In the context of VPNs, TLS is often used to secure the communication channel between the client and the server. This ensures that data transmitted over the VPN is encrypted and protected from eavesdropping. TLS-based VPNs, such as OpenVPN, are popular for their strong security and flexibility.
The Importance of Digital Certificates
Digital certificates play a vital role in TLS by providing a means to authenticate the identities of parties involved in a communication. These certificates are issued by trusted entities known as Certificate Authorities (CAs). When a client connects to a server, it can verify the server’s certificate to ensure it is communicating with the intended party.
TLS and Perfect Forward Secrecy (PFS)
Perfect Forward Secrecy (PFS) is a feature that ensures session keys are not compromised even if the server’s private key is exposed in the future. TLS supports PFS through the use of ephemeral key exchanges, such as Elliptic Curve Diffie-Hellman (ECDHE). Implementing PFS enhances the security of TLS connections by protecting past communications.
Common TLS Vulnerabilities
While TLS provides strong security, it is not immune to vulnerabilities:
- Heartbleed: A bug in the OpenSSL library that allowed attackers to read sensitive data from affected servers.
- POODLE: An attack that exploited vulnerabilities in SSL 3.0, leading to its deprecation.
- FREAK: A vulnerability that allowed attackers to force servers to use weak encryption keys.
Regularly updating software and using strong cryptographic algorithms can mitigate these risks.
Best Practices for Using TLS
To ensure the effectiveness of TLS in securing communications:
- Use the latest version of TLS (preferably TLS 1.3).
- Employ strong encryption algorithms and key lengths.
- Regularly update and patch software to fix known vulnerabilities.
- Use certificates from trusted Certificate Authorities.
- Implement Perfect Forward Secrecy to protect past communications.
Conclusion
Transport Layer Security (TLS) is a fundamental protocol that ensures secure communication over the internet. By encrypting data and authenticating identities, TLS protects sensitive information from unauthorized access. Understanding how TLS works and implementing best practices can help maintain the privacy and integrity of online communications.