In today’s digital age, websites and online services are essential for businesses and individuals alike. However, these services face various threats, one of the most disruptive being Distributed Denial-of-Service (DDoS) attacks. Understanding DDoS attacks is crucial for anyone involved in managing or using online platforms.
What is a DDoS Attack?
A DDoS attack is a malicious attempt to overwhelm a server, network, or system by flooding it with excessive traffic from multiple sources. The primary goal is to exhaust the target’s resources, rendering it unavailable to legitimate users. Unlike traditional Denial-of-Service (DoS) attacks, which originate from a single source, DDoS attacks come from numerous compromised devices distributed across the internet.
How Do DDoS Attacks Work?
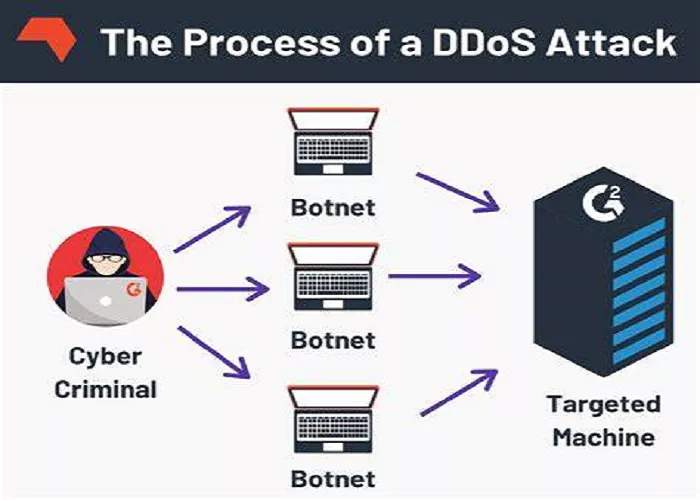
Attackers employ various methods to execute DDoS attacks, often utilizing botnets—networks of infected devices controlled remotely. These botnets can consist of thousands or even millions of devices, including computers, smartphones, and Internet of Things (IoT) devices like cameras and routers. Once a device is infected, it becomes part of the botnet and can be used to send massive amounts of traffic to the target without the device owner’s knowledge.
The coordinated traffic from these devices overwhelms the target’s infrastructure, leading to service degradation or complete outages. The distributed nature of these attacks makes them challenging to defend against, as the malicious traffic comes from many different sources, masking the attack’s origin.
Types of DDoS Attacks
DDoS attacks can be broadly categorized based on the layer of the OSI model they target:
1. Volumetric Attacks
These attacks aim to consume the target’s bandwidth by generating high volumes of traffic. Common techniques include:
- UDP Floods: Sending large volumes of User Datagram Protocol (UDP) packets to random ports on the target system, causing the system to check for application listening at those ports and respond with ICMP Destination Unreachable packets, thereby consuming bandwidth.
- ICMP Floods: Overwhelming the target with Internet Control Message Protocol (ICMP) Echo Request (ping) packets, consuming both incoming and outgoing bandwidth.
- DNS Amplification: Exploiting DNS servers to flood a target with DNS response traffic, amplifying the attack’s impact.
2. Protocol Attacks
These attacks exploit weaknesses in network protocols to consume server or network device resources. Examples include:
- SYN Floods: Sending a succession of SYN requests to a target’s system in an attempt to overwhelm it.
- Smurf Attacks: Sending a large number of ICMP packets with the victim’s IP address as the source address, causing systems to flood the victim with responses.
- Ping of Death: Sending malformed or oversized packets using a ping command, causing buffer overflows and system crashes.
3. Application Layer Attacks
These attacks target the application layer (Layer 7) of the OSI model, aiming to exhaust server resources by mimicking legitimate user behavior. Examples include:
- HTTP Floods: Sending seemingly legitimate HTTP GET or POST requests to attack a web server or application.
- Slowloris: Keeping many connections to the target web server open and holding them open as long as possible, causing the server to exhaust its connection pool and deny service to legitimate users.
Notable DDoS Attacks in History
Several high-profile DDoS attacks have highlighted the potential severity of such threats:
- Estonia (2007): A series of DDoS attacks targeted Estonian government, media, and banking websites, crippling the nation’s online infrastructure for weeks.
- Sony PlayStation Network (2014): Attackers overwhelmed Sony’s gaming network with a massive DDoS attack, causing a significant outage during the holiday season.
- Dyn DNS Attack (2016): A massive DDoS attack using the Mirai botnet disrupted Dyn, a major DNS provider, affecting major websites like Twitter, Netflix, and Reddit.
Mitigation Strategies
Protecting against DDoS attacks requires a multi-layered approach:
- Traffic Analysis: Implementing systems that monitor and analyze traffic patterns to detect anomalies indicative of DDoS attacks.
- Rate Limiting: Setting up rate limiting to control the amount of traffic a server will accept from a single IP address within a specified timeframe.
- Geographical Blocking: Blocking or restricting traffic from regions where no legitimate traffic is expected.
- Content Delivery Networks (CDNs): Utilizing CDNs to distribute traffic across multiple servers, mitigating the impact of localized DDoS attacks.
- DDoS Protection Services: Engaging with specialized DDoS protection services that can absorb and mitigate large-scale attacks.
Conclusion
DDoS attacks pose significant threats to the availability and reliability of online services. Understanding their mechanisms, types, and historical impact is essential for developing effective mitigation strategies. As cyber threats continue to evolve, staying informed and prepared is crucial for anyone involved in the digital landscape.