Virtual Private Networks (VPNs) are widely used tools designed to enhance online privacy and security by encrypting a user’s internet connection and masking their IP address. They are particularly popular among individuals and organizations seeking to protect sensitive data and maintain anonymity while browsing the internet. However, despite their advantages, the question arises: can hackers still infiltrate systems through a VPN? This article delves into the potential vulnerabilities of VPNs, explores scenarios where they might be compromised, and offers guidance on mitigating associated risks.
What is VPNs and Their Purpose
A VPN creates a secure, encrypted tunnel between a user’s device and a VPN server, routing the user’s internet traffic through this tunnel to safeguard data from external threats. This process serves multiple purposes:
- Data Encryption: Protects data from interception by encrypting the connection, making it difficult for unauthorized parties to access the transmitted information.
- IP Address Masking: Hides the user’s real IP address, replacing it with the VPN server’s IP address, thereby enhancing anonymity.
- Bypassing Geo-Restrictions: Allows access to content restricted to certain geographic locations by making it appear as though the user is accessing the internet from the VPN server’s location.
Potential Vulnerabilities in VPNs
While VPNs offer significant security benefits, they are not entirely immune to hacking attempts. Several vulnerabilities can be exploited by malicious actors:
1. Weak Encryption Protocols
Some VPNs may use outdated or weak encryption standards, making them susceptible to cryptographic attacks. Attackers can exploit these weaknesses to decrypt data and gain unauthorized access. For instance, vulnerabilities in VPN protocols like SSTP have been identified, with over 90% of detected servers being vulnerable to TLS downgrade attacks.
2. Malware-Infected VPN Clients
Not all VPN services maintain rigorous security practices. Some VPN applications may themselves be compromised or contain malware, posing significant risks to users. There have been instances where VPN apps, such as Turbo VPN and VPN Proxy Master, were found to be linked to entities involved in data harvesting, raising concerns about user privacy and data security.
3. DNS and IP Leaks
Even when connected to a VPN, certain leaks can occur:
- DNS Leaks: Reveal the user’s browsing activity to the DNS server, potentially exposing visited websites.
- IP Leaks: Expose the user’s real IP address despite the VPN connection, compromising anonymity.
These leaks can undermine the privacy that VPNs aim to provide.
4. Compromised VPN Servers
If a VPN provider’s servers are compromised, attackers can potentially monitor or manipulate the traffic passing through them. There have been cases where vulnerabilities in VPN appliances, such as Ivanti’s Connect Secure VPN, were exploited by state-sponsored groups, leading to unauthorized access and data breaches.
5. Endpoint Device Vulnerabilities
A VPN secures data in transit but does not protect the device itself. If a user’s device is infected with malware, attackers can bypass VPN protections. Therefore, the security of the endpoint device is crucial in maintaining overall security.
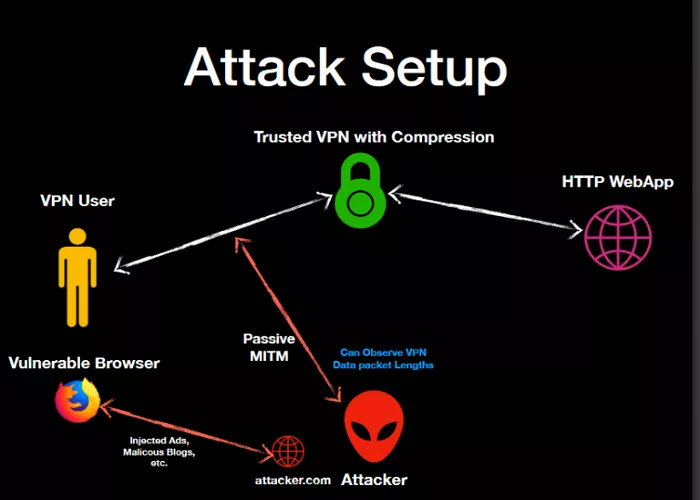
6. Man-in-the-Middle (MitM) Attacks
Attackers positioned between the user and the VPN server can intercept and potentially alter communications. While encryption mitigates this risk, vulnerabilities in the VPN’s implementation can be exploited to carry out MitM attacks.
Real-World Examples of VPN Vulnerabilities
Understanding the practical implications of VPN vulnerabilities can shed light on potential risks:
- Cisco ASA Vulnerabilities: In 2024, state-sponsored hackers exploited zero-day vulnerabilities in Cisco’s Adaptive Security Appliances (ASA), which are VPN devices used globally, to gain persistent access to government networks.
- ArcaneDoor Campaign: This campaign targeted VPN devices to infiltrate networks, demonstrating how vulnerabilities in VPN hardware can be exploited for espionage.
Mitigating VPN Security Risks
To enhance security while using VPNs, consider the following measures:
- Choose Reputable VPN Providers: Select VPN services known for strong security practices, transparent policies, and regular audits.
- Keep Software Updated: Regularly update VPN client applications and the device’s operating system to patch known vulnerabilities.
- Use Strong Encryption Protocols: Opt for VPNs that utilize robust encryption standards, such as AES-256, to protect data effectively.
- Enable Leak Protection: Ensure that the VPN service offers DNS and IP leak protection to maintain privacy.
- Secure Endpoint Devices: Use reputable security software to protect devices from malware and other threats that could compromise VPN security.
- Stay Informed About VPN Vulnerabilities: Keep abreast of security advisories related to VPN services and apply recommended patches promptly.
Conclusion
While VPNs significantly enhance online privacy and security, they are not impervious to hacking attempts. Understanding the potential vulnerabilities associated with VPN usage is essential for users seeking to protect their data and maintain anonymity online. By selecting reputable VPN providers, maintaining updated software, and implementing comprehensive security measures, users can mitigate the risks and enjoy the benefits that VPNs offer.