In today’s digital age, online privacy and security are more important than ever. Many individuals seek ways to protect their personal information from prying eyes. Two popular tools for enhancing online anonymity are Tor and Virtual Private Networks (VPNs). But what happens when you combine them? Is using Tor over a VPN safe? Let’s explore this setup in detail.
What is Tor and VPN
Before diving into the safety of using Tor over a VPN, it’s essential to understand what each tool does.
What is Tor?
Tor, short for “The Onion Router,” is a free, open-source software that enables anonymous communication on the internet. It achieves this by routing your internet traffic through a series of volunteer-operated servers, known as nodes, which obscure your IP address and encrypt your data multiple times. This layered encryption is why it’s often referred to as “onion routing.” Tor is particularly useful for accessing websites on the dark web and for users in regions with heavy internet censorship.
What is a VPN?
A Virtual Private Network (VPN) is a service that creates a secure, encrypted connection between your device and a VPN server. This connection masks your IP address, making it appear as though your internet traffic is coming from the VPN server rather than your actual location. VPNs are commonly used to protect data on public Wi-Fi networks, bypass geographic restrictions, and maintain privacy from Internet Service Providers (ISPs).
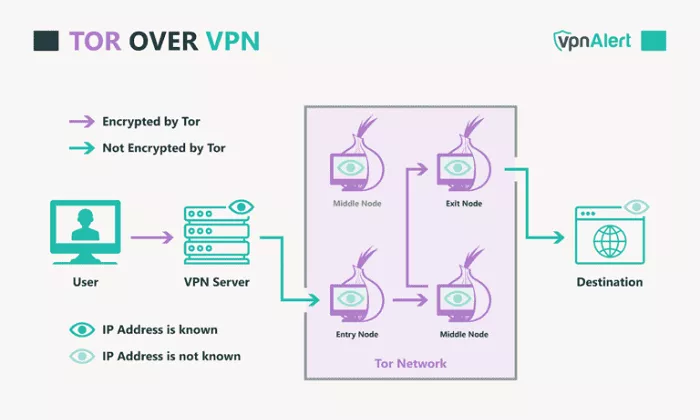
How Does Tor Over VPN Work?
When you use Tor over a VPN, your internet traffic first passes through the VPN server, which encrypts your data and hides your IP address. After this, the encrypted traffic enters the Tor network, where it is routed through multiple nodes, further anonymizing your connection. This setup provides an additional layer of security, as even if someone monitors the Tor network, they cannot easily trace your original IP address.
Is Tor Over VPN Safe?
Using Tor over a VPN offers several security advantages:
Enhanced Anonymity: The VPN hides your IP address from the Tor entry node, making it more challenging to trace your internet activity back to you.
Protection from Malicious Exit Nodes: Tor exit nodes can potentially monitor unencrypted traffic leaving the network. By using a VPN, your data remains encrypted until it reaches the VPN server, reducing the risk of exposure.
Bypassing ISP Restrictions: Some ISPs may block or throttle Tor traffic. Using a VPN can help circumvent these restrictions, allowing you to access the Tor network without interference.
However, there are also considerations to keep in mind:
Trust in VPN Provider: Your VPN provider can see your real IP address and the websites you visit. It’s crucial to choose a reputable VPN service with a strict no-logs policy to ensure your privacy is maintained.
Potential Speed Reduction: Both Tor and VPNs can slow down your internet connection due to the encryption and routing processes. Combining them may result in a more noticeable decrease in speed.
Legal and Policy Implications: In some countries, the use of Tor is monitored or restricted. Always be aware of and comply with local laws and regulations regarding internet usage.
Best Practices for Using Tor Over VPN
To maximize the benefits and minimize the risks of using Tor over a VPN, consider the following best practices:
Choose a Trustworthy VPN Provider: Opt for a VPN service with a proven track record of protecting user privacy and a clear, enforceable no-logs policy.
Use Secure VPN Protocols: Ensure your VPN uses strong encryption protocols, such as OpenVPN or WireGuard, to protect your data.
Enable Kill Switch Features: A kill switch ensures that your internet connection is severed if the VPN connection drops, preventing accidental exposure of your real IP address.
Regularly Update Software: Keep your VPN and Tor software up to date to protect against known vulnerabilities.
Be Cautious with Personal Information: Even with enhanced anonymity, avoid sharing personal details online that could compromise your identity.
Conclusion
Tor over a VPN can provide an additional layer of security and privacy for users seeking enhanced anonymity online. While it offers several advantages, it’s essential to be aware of the potential risks and limitations associated with this setup. By choosing a reputable VPN provider and following best practices, you can significantly improve your online privacy and security.
Remember, no single tool can guarantee complete anonymity. Combining Tor with a VPN is a powerful strategy, but it’s most effective when used as part of a broader approach to online privacy.