In today’s digital age, ensuring secure and private internet connections is more important than ever. Virtual Private Networks (VPNs) play a crucial role in safeguarding online activities. One of the earliest VPN protocols developed is the Point-to-Point Tunneling Protocol (PPTP). This article provides a comprehensive overview of PPTP, explaining its workings, advantages, disadvantages, and current relevance.
What Is PPTP?
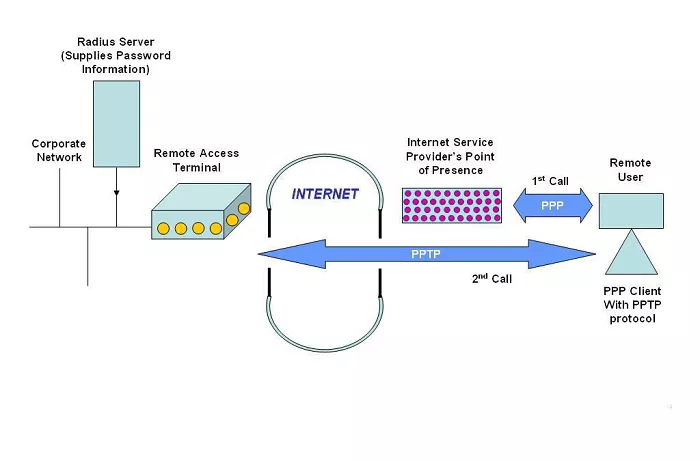
PPTP stands for Point-to-Point Tunneling Protocol. Developed by Microsoft in the mid-1990s, it was designed to enable secure data transmission over public networks like the internet. PPTP creates a virtual tunnel between the user’s device and the VPN server, allowing data to pass through securely.
How Does PPTP Work?
PPTP operates by encapsulating data packets within other packets, creating a “tunnel” through which data can travel securely. It uses a combination of a control channel over TCP and a tunnel over Generic Routing Encapsulation (GRE) to encapsulate PPP packets. This method allows for the secure transmission of data from one point to another over the internet.
Advantages of PPTP
1. Easy Setup
One of PPTP’s main advantages is its simplicity. It is natively supported by many operating systems, including Windows, macOS, Linux, and various mobile platforms. This widespread compatibility makes it easy to set up without the need for additional software or complex configurations.
2. Fast Connection Speeds
PPTP is known for its high-speed connections. Due to its relatively low encryption overhead, it offers faster data transmission compared to some other VPN protocols. This makes it suitable for activities that require high bandwidth, such as streaming and online gaming.
3. Compatibility with Older Systems
Given its age, PPTP is compatible with many older devices and operating systems. This makes it a viable option for users operating legacy systems that may not support newer VPN protocols.
4. Suitable for Basic Use
For users who require a VPN for basic tasks, such as accessing geo-restricted content or bypassing simple network restrictions, PPTP can be an effective solution.
Disadvantages of PPTP
1. Weak Security
Despite its advantages, PPTP has significant security vulnerabilities. The encryption methods used by PPTP, such as Microsoft’s Point-to-Point Encryption (MPPE), are considered outdated and susceptible to various attacks. Security experts have identified weaknesses in the protocol that can be exploited by attackers to intercept and decrypt data.
2. Susceptibility to Attacks
PPTP is vulnerable to several types of cyberattacks, including brute-force attacks and dictionary attacks. These vulnerabilities stem from the use of weak authentication protocols like MS-CHAP v1 and v2, which can be compromised by attackers to gain unauthorized access to data.
3. Limited Firewall Traversal
PPTP uses GRE for tunneling, which is not always supported by all network configurations. As a result, PPTP connections can be easily blocked by firewalls that do not allow GRE traffic, limiting its usability in certain environments.
4. Obsolescence
Due to its security flaws and the availability of more secure alternatives, PPTP is considered obsolete by many in the cybersecurity community. Modern VPN protocols offer better encryption and more robust security features, making them preferable choices for protecting sensitive data.
Security Concerns
Encryption Weaknesses
PPTP relies on MPPE for encryption, which uses the RC4 cipher. RC4 has known vulnerabilities and is no longer considered secure. Additionally, the use of SHA-1 for hashing in PPTP is problematic, as SHA-1 has been deprecated due to its susceptibility to collision attacks.
Authentication Issues
The authentication mechanisms used in PPTP, particularly MS-CHAP v1 and v2, have been compromised. Attackers can exploit these weaknesses to perform man-in-the-middle attacks, intercepting and potentially altering data transmitted over the VPN.
Lack of Forward Secrecy
PPTP does not support forward secrecy, meaning that if an encryption key is compromised, all past and future communications encrypted with that key are also compromised. This lack of forward secrecy poses a significant risk to data confidentiality.
Use Cases for PPTP
Despite its shortcomings, PPTP may still be suitable for certain use cases:
- Streaming Content: For users looking to access geo-restricted streaming services without transmitting sensitive data, PPTP’s fast speeds can be beneficial.
- Bypassing Simple Network Restrictions: In environments where network restrictions are minimal, PPTP can help users access blocked websites or services.
- Compatibility with Legacy Systems: Organizations using older hardware or software that does not support modern VPN protocols may find PPTP to be a viable option.
However, it’s important to note that these use cases involve scenarios where security is not the primary concern.
Alternatives to PPTP
Given the security vulnerabilities associated with PPTP, several more secure VPN protocols are recommended:
1. L2TP/IPsec
Layer 2 Tunneling Protocol (L2TP) combined with IPsec provides enhanced security features, including stronger encryption and better authentication mechanisms. It is widely supported and offers a good balance between security and performance.
2. OpenVPN
OpenVPN is an open-source VPN protocol known for its robust security and flexibility. It uses SSL/TLS for key exchange and supports a variety of encryption algorithms, making it suitable for securing sensitive data.
3. IKEv2/IPsec
Internet Key Exchange version 2 (IKEv2) paired with IPsec offers strong security and stability, especially for mobile users. It supports automatic reconnection and is resistant to network changes, making it ideal for users on the move.
4. WireGuard
WireGuard is a modern VPN protocol that aims to provide high-speed connections with state-of-the-art cryptography. It is designed to be simple, fast, and secure, making it a promising alternative to traditional VPN protocols.
Conclusion
PPTP played a significant role in the early development of VPN technology, offering a simple and fast solution for secure remote connections. However, due to its numerous security vulnerabilities and the availability of more secure alternatives, PPTP is no longer recommended for protecting sensitive data. Users and organizations should consider transitioning to modern VPN protocols like OpenVPN, IKEv2/IPsec, or WireGuard to ensure robust security and privacy in today’s digital landscape.